S3 Bucket
To minimize latency, we recommend creating your S3 bucket in the us-east-1 region, as our systems are currently located there. However, your bucket can be located anywhere, and we plan to expand our geographical presence in the future.Creating the bucket
Name the bucket according to your own business standards. For this example, we will name itdemo-pz-code-sharing.
1
Name the bucket
Set it to be a general purpose bucket.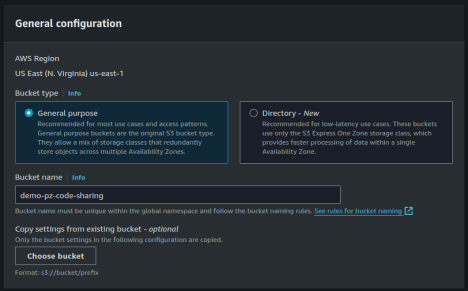

2
Access Controls
ACLs disabled (recommended)

3
Disable bucket versioning
If data is deleted, it can be recreated from scratch.
4
Default encryption
Enable default encryption with server-side encryption according to the security policies specified by your organization. In this example, we will use the default.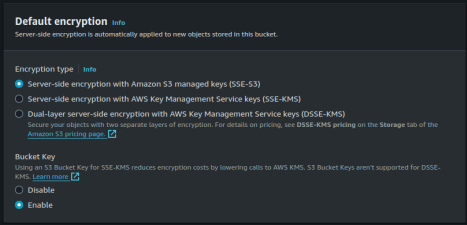

5
Disable Object Lock
We require that Object Lock be disabled, as enabling it will greatly reduce performance.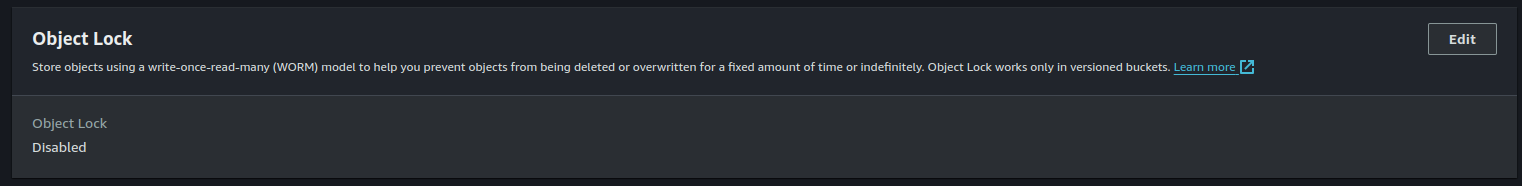

6
Finish creating the bucket
Now that we completed creating the bucket, now we need to create an API token to give PlayerZero to read and write.
Create an API Token
1
Create a new user group
Using the IAM console, create a new user group called
playerzero.
Add your API user to this group if one already exists, or create a new user as described below.2
Set Permission Policy
For the permission policy, add the AmazonS3FullAccess policy to this group. This will grant PlayerZero full access to your S3 bucket.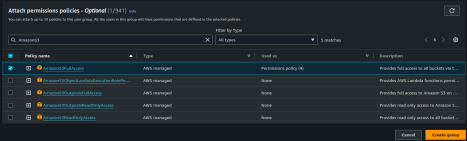

3
Create a New User
Create a new user called 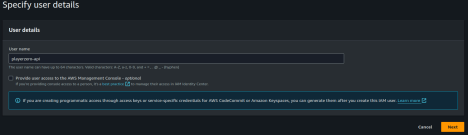
playerzero-api to easily manage access and restrictions without affecting other users or systems. Do not grant this user access to the Management Console.
4
Associate User Group
Associate the
playerzero-api user with the appropriate user group playerzero containing the AmazonS3FullAccess policy.5
Create Access Key
Edit the newly created 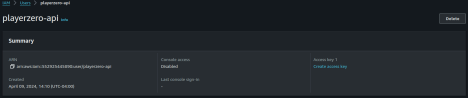
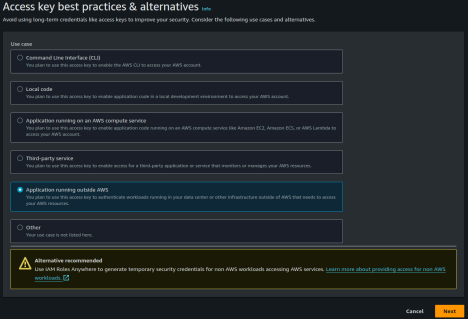
playerzero-api user and click on the Create access key link in the summary box. Create an access key for an application running outside AWS to use.

6
Provide a Description
Provide an appropriate description, such as PlayerZero Access, and create the access key.
7
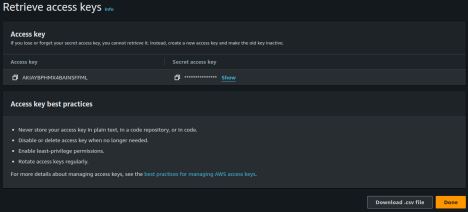
Obtain Access Keys
You will be shown a screen with the Access Key and the Secret Access Key. It is not possible to obtain the secret key after this screen. Copy both keys and share them with PlayerZero securely.